Workaround Instructions for CVE-2021-21972 and CVE-2021-21973 on VMware vCenter Server
Article ID: 317865
Updated On:
Products
VMware vCenter Server
Issue/Introduction
The vCenter Server team has investigated CVE-2021-21972 and CVE-2021-21973 and have determined that the possibility of exploitation can be removed by performing the steps detailed in the Workaround section of this article. This workaround is meant to be a temporary solution until updates documented in VMSA-2021-0002 can be deployed.
Impacted and Fixed vCenter Server Versions:
The links below provide detailed instructions on how to upgrade your VCSA machines.
vSphere 6.7
https://communities.vmware.com/t5/vSphere-Upgrade-Install/Addressing-VMSA-2021-0002-for-vCenter-6-7/ta-p/2833192
vSphere 7.0
https://communities.vmware.com/t5/vSphere-Upgrade-Install/Addressing-VMSA-2021-0002-for-vCenter-7-0/ta-p/2833079
For any queries with the procedure to update VMware vCenter , please open a thread in the VMTN using this link
Impacted and Fixed vCenter Server Versions:
| Version | Impacted Versions | Fixed Version | Release Date | VAMI/Release Notes Build Number | Client/MOB/vpxd.log Build Number |
| 7.0 | All versions prior to 7.0 U1c | 7.0 U1c (or later) | 2020-12-17 | 17327517 (or later) | 17327586 (or later) |
| 6.7 VCSA | All versions prior to 6.7 U3l | 6.7 U3l (or later) | 2020-11-19 | 17138064 (or later) | 17137327 (or later) |
| 6.7 Windows | All versions prior to 6.7 U3l | 6.7 U3l (or later) | 2020-11-19 | 17138064 (or later) | 17137232 (or later) |
| Version | Impacted Version | Fixed Version | Release Date | Build Number |
| 6.5 (VCSA and Windows) | All versions prior to 6.5 U3n | 6.5 U3n (or later) | 2021-02-23 | 17590285(or later) |
The links below provide detailed instructions on how to upgrade your VCSA machines.
vSphere 6.7
https://communities.vmware.com/t5/vSphere-Upgrade-Install/Addressing-VMSA-2021-0002-for-vCenter-6-7/ta-p/2833192
vSphere 7.0
https://communities.vmware.com/t5/vSphere-Upgrade-Install/Addressing-VMSA-2021-0002-for-vCenter-7-0/ta-p/2833079
For any queries with the procedure to update VMware vCenter , please open a thread in the VMTN using this link
Functionality Impacts:
Functionality impacts are limited to environments that use vRealize Operations. It should be noted that the vulnerable endpoint exists in vCenter Server whether or not vRealize Operations has ever been introduced to the environment.
- New vRealize Operations customers will not have the provision/option to auto install & configure the vRealize Operations Appliance through the plugin.
- Customers who have already configured a vCenter Adapter in vRealize Operations with vCenter will not be able to display the metric & alert details (both vCenter Server & vSAN overview widgets) in the vSphere Client (HTML 5).
Resolution
Resolution for CVE-2021-21972 and CVE-2021-21973 is documented in VMSA-2021-0002.
Workaround:
To implement the workaround for CVE-2021-21972 and CVE-2021-21973 on Linux-based virtual appliances (vCSA) perform the following steps:
The plugin must be set to "incompatible". Disabling the plugin from within the UI will not protect the system from this vulnerability.
This workaround is required to be carried out on both the active and passive node in environments running vCenter High Availability (VCHA)
</pluginsCompatibility>

</pluginsCompatibility>
</pluginsCompatibility>
</pluginsCompatibility>
Workaround:
To implement the workaround for CVE-2021-21972 and CVE-2021-21973 on Linux-based virtual appliances (vCSA) perform the following steps:
The plugin must be set to "incompatible". Disabling the plugin from within the UI will not protect the system from this vulnerability.
This workaround is required to be carried out on both the active and passive node in environments running vCenter High Availability (VCHA)
- Connect to the vCSA using an SSH session and root credentials.
- Backup the /etc/vmware/vsphere-ui/compatibility-matrix.xml file:
cp -v /etc/vmware/vsphere-ui/compatibility-matrix.xml /etc/vmware/vsphere-ui/compatibility-matrix.xml.backup
- Open the compatibility-matrix.xml file in a text editor:
vi /etc/vmware/vsphere-ui/compatibility-matrix.xml
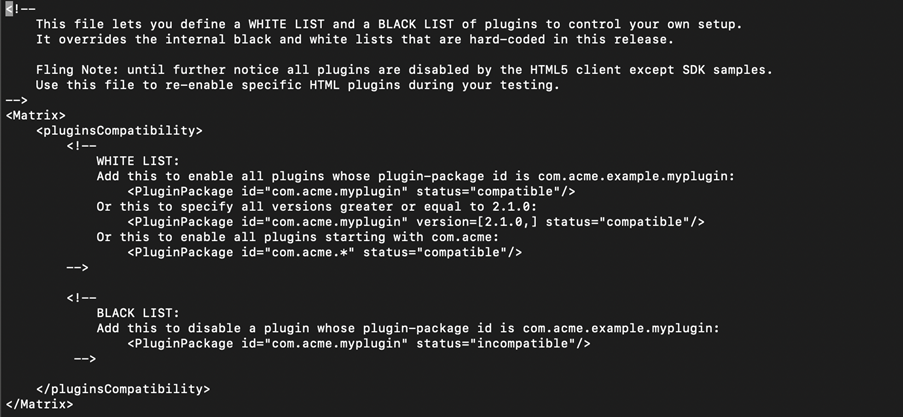
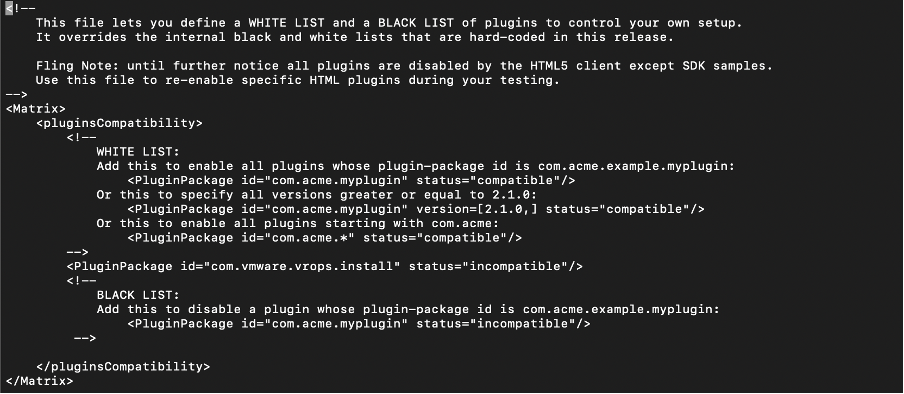
- Content of this file looks like below :
- Add the following:
<Matrix>
<pluginsCompatibility>
. . . .
. . . .
<PluginPackage id="com.vmware.vrops.install" status="incompatible"/>
</pluginsCompatibility>
</Matrix>
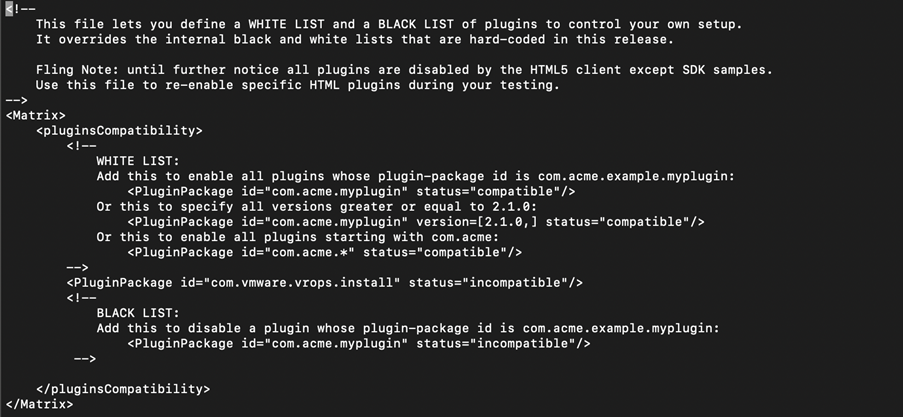
- The file should like below:
- Save and close the compatibility-matrix.xml file by typing: :wq!
- Stop and restart the vsphere-ui service using the commands:
- service-control --stop vsphere-ui.
- service-control --start vsphere-ui.
- Navigate to the https://<VC-IP-or-FQDN>/ui/vropspluginui/rest/services/checkmobregister. This page displays 404/Not Found error (as shown below).
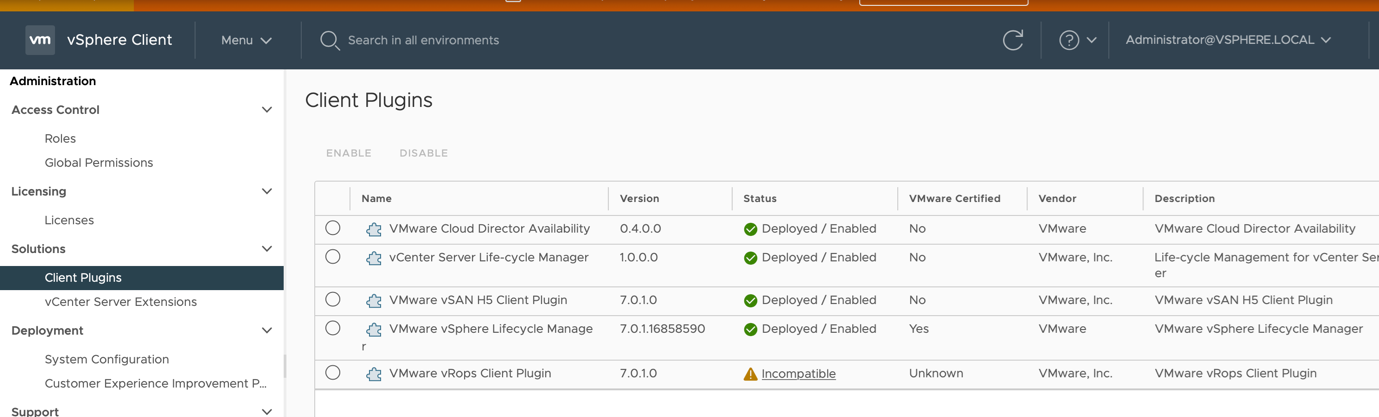
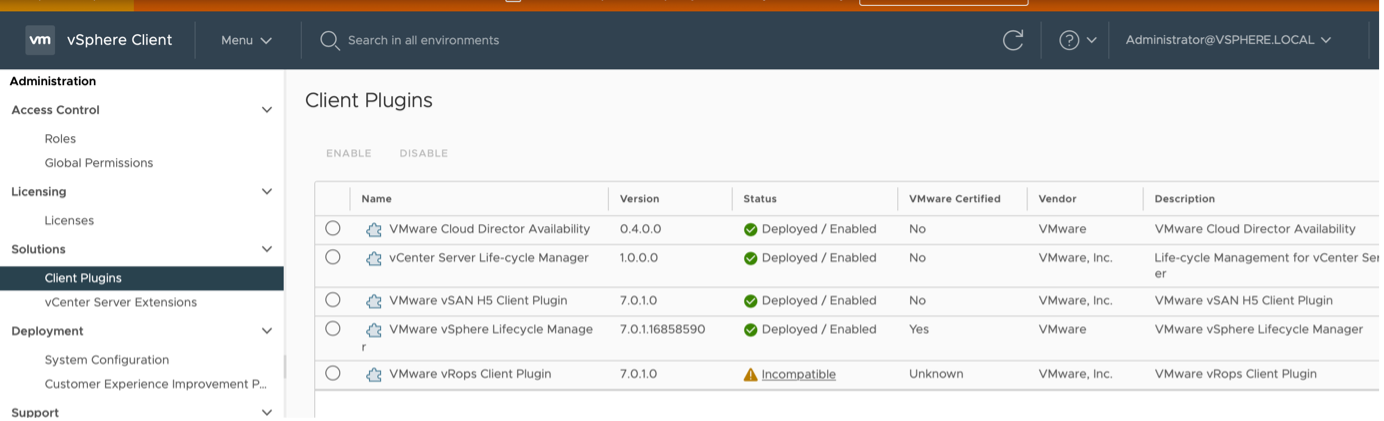
- From the vSphere Client (HTML5), the VMware vROPS Client plugin can be seen as “incompatible” under Administration > Solutions > client-plugins as shown below
- This confirms that the endpoint /ui/vropspluginui is set to "incompatible".
To implement the workaround for CVE-2021-21972 and CVE-2021-21973 on Windows-based vCenter Server deployments perform the following steps:
(The plugin must be set to "incompatible". Disabling the plugin from within the UI will not protect the system from this vulnerability)
(The plugin must be set to "incompatible". Disabling the plugin from within the UI will not protect the system from this vulnerability)
- RDP to the windows based vCenter Server.
- Take a backup of the file –
C:\ProgramData\VMware\vCenterServer\cfg\vsphere-ui\compatibility-matrix.xml
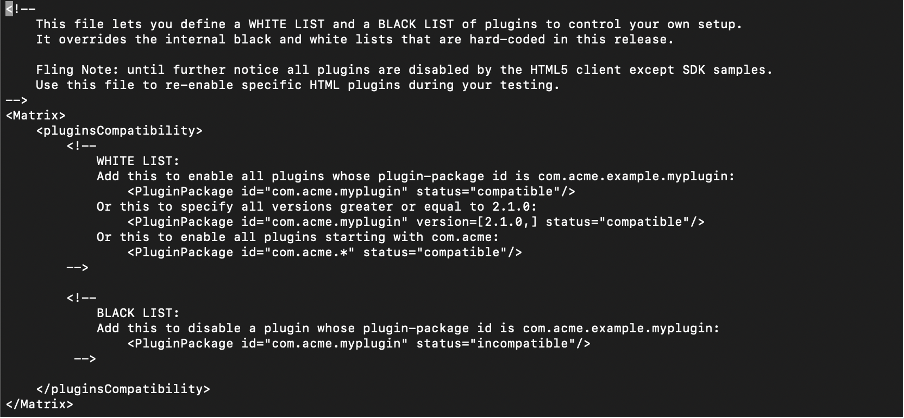
- Content of this file looks like below:
- Add the following:
<Matrix>
<pluginsCompatibility>
. . . .
. . . .
<PluginPackage id="com.vmware.vrops.install" status="incompatible"/>
</pluginsCompatibility>
</Matrix>
- The file should look like below:
- Stop and restart the vsphere-ui service using the commands:
- C:\Program Files\VMware\vCenter Server\bin> service-control --stop vsphere-ui
- C:\Program Files\VMware\vCenter Server\bin> service-control --start vsphere-ui
- From a web browser, navigate to:
https://<VC-IP-or-FQDN>/ui/vropspluginui/rest/services/checkmobregister.
This page displays 404/Not Found error (as shown below):

This page displays 404/Not Found error (as shown below):
- From the vSphere Client (HTML 5), the VMware vROPS Client plugin can be seen as “incompatible” under Administration > Solutions > client-plugins as shown below:
- This confirms that the endpoint /ui/vropspluginui is set to "incompatible".
To revert the workaround for CVE-2021-21972 and CVE-2021-21973 on Linux-based virtual appliances (vCSA) perform the following steps:
- Connect to the vCSA with an SSH session and root credentials.
- Open the compatibility-matrix.xml file in a text editor:
vi /etc/vmware/vsphere-ui/compatibility-matrix.xml
- Remove the below line in the file.
<Matrix>
<pluginsCompatibility>
. . . .
. . . .
<PluginPackage id="com.vmware.vrops.install" status="incompatible"/>
</pluginsCompatibility>
</Matrix>
- Stop and restart the vsphere-ui service using the commands:
- service-control --stop vsphere-ui.
- service-control --start vsphere-ui
- Validate that the vSphere-ui service is up.
- The VMware vROPS Client plugin status is deployed/enabled
To revert the workaround for CVE-2021-21972 and CVE-2021-21973 on Windows-based vCenter Server deployments perform the following steps:
- Connect to the Windows vCenter Server.
- Using a text editor edit the file:
C:\ProgramData\VMware\vCenterServer\cfg\vsphere-ui\compatibility-matrix.xml
- Remove the below line in the file.
<Matrix>
<pluginsCompatibility>
. . . .
. . . .
<PluginPackage id="com.vmware.vrops.install" status="incompatible"/>
</pluginsCompatibility>
</Matrix>
- Stop and restart the vsphere-ui service using the commands:
- C:\Program Files\VMware\vCenter Server\bin> service-control --stop vsphere-ui
- C:\Program Files\VMware\vCenter Server\bin> service-control --start vsphere-ui
- Validate that the vSphere-ui service is up.
- The VMware vROPS Client plugin status is deployed/enabled
- For more information on how to start/stop/restart services see;
Additional Information
For up-to-date information on CVE-2021-21972 and CVE-2021-21973 as well as future security information please sign up for VMware Security Advisory announcements at our mailing list portal. RSS feeds are also available on the advisories themselves.
How to Disable/Enable CIM Server on VMware ESXi
How to Disable/Enable CIM Server on VMware ESXi
Feedback
Yes
No
